
NSF SECURE Center: Northeastern selected as the Northeast regional lead for the National Science Foundation’s (NSF) new SECURE Center
Northeastern University has been selected as the Northeast regional lead for the National Science Foundation’s (NSF) new SECURE Center. The SECURE Center grant was awarded to the University of Washington with a start date of September 1, 2024. The SECURE Center award from NSF provides almost $50 million in funding for the University of Washington and its partners to provide research security tools, training and awareness for the United States. SECURE (Safeguarding the Entire Community in the U.S. Research Ecosystem) will take a community-centered approach, focusing on input from stakeholders across the research enterprise, including small businesses, faculty, and academic institutions of all types. Northeastern will lead the activities for the Northeast region, ranging from Maine to Washington, D.C.
You can learn more about the NSF SECURE Center and how it will support research security and international collaboration here. If you would like to engage in NSF SECURE, please complete the contact form on the University of Washington page.
Any questions or concerns about Northeastern’s role in NSF’s SECURE Center can be sent to secureNE@northeastern.edu.
Recent Regulatory Updates

NEW: Annual Malign Foreign Talent Recruitment Program Certification for PIs/co-PIs
Starting on June 7, 2025, in accordance with the NSF Proposal and Award Policies and Procedures Guide (PAPPG) Chapter II.D.1.e(ii), all PIs or co-PIs named on an NSF award made on or after May 20, 2024, must certify annually in Research.gov that they are not party to a MFTRP. Individuals who are currently a party to a MFTRP are not eligible to serve as senior/key personnel on an NSF proposal or on any NSF award made on or after May 20, 2024. NSF is providing notification of this new requirement to impacted PIs and co-PIs.
Key points
There is no organizational certification requirement, the certification requirement is for PIs and co-PIs.
Impacted PIs and co-PIs will be prompted to complete the MFTRP certification after signing into Research.gov using the Sign In link at the top of www.Research.gov.
PIs and co-PIs with more than one active award made on or after May 20, 2024, are only required to certify once, annually.
Once completed, PIs and co-PIs can view their MFTRP certification response under the Academic/Professional Information section of their profile.
NSF is working to expand the MFTRP annual certification requirement for all senior/key personnel roles at a future date. Additionally, NSF is working to provide organizations with access to the annual certifications.
Please see PAPPG Chapter II.D.1.d(ix) for information about Authorized Organizational Representative (AOR) responsibilities regarding senior/key personnel MFTRP certifications.
Frequently Asked Questions and MFTRP contract examples will be available on the MFTRP section of the Office of the Chief of Research Security Strategy and Policy website shortly.

Compliance with Polices surrounding Malign Foreign Talent Recruitment Programs
In accordance with the National Science Foundation (NSF), Department of Defense (DOD), and Department of Energy (DOE), Northeastern University has updated its Policy on External International Engagements to reflect the restriction on participation in Malign Foreign Talent Recruitment Programs (MFTRP) as defined by the CHIPS & Science Act of 2022. The Office of the Provost has the authority to determine if an Foreign Talent Recruitment Program (FTRP) meets the definition of a MFRTP. If a faculty member is a participant in a FTRP that meets the definition of a MFRTP, that faculty member will be restricted from participating in any current research efforts that are federally funded and/or applying for any federally funded research grants. Additional information on FTRPs and MFTRPs can be found here.

NSF TRUST Framework
The National Science Foundation (NSF) has announced a new risk mitigation process, the Trusted Research Using Safeguards and Transparency (TRUST) framework. This framework will help the agency assess grant proposals for potential national security risks. The TRUST process will be rolled out in three phases beginning in FY 2025 with a process piloted on quantum-related proposals. You can learn more about the TRUST framework and BIS export control quantum updates here.

Final Guidelines for Research Security Programs at Covered Institutions
OSTP released the final Guidelines for Research Security Programs at Covered Institutions on July 9, 2024. Within six months of the issuance of this memorandum, federal research agencies have been instructed to submit to OSTP and OMB plans for updating policies to ensure this guidance is reflected in the Research Security Programs Standard Requirements of each federal research agency. Updated policies of federal research agencies shall take effect no later than six months after finalized plans have been submitted to OSTP and OMB. Federal research agencies shall ensure that covered institutions have adequate time, but not more than 18 months after the effective date of their plans, to implement the requirements of this memorandum.

Prohibition on Unmanned Aircraft Systems from Covered Foreign Entities
On November 12, 2024, the Department of Defense (DoD), the General Services Administration (GSA), and the National Aeronautics and Space Administration (NASA) published Interim Rule “Prohibition on Unmanned Aircraft Systems from Covered Foreign Entities” (FAR Case 2024-002) prohibiting the procurement, operation, or use of Federal funds on UAS prohibited by the Federal Acquisition Security Council (FASC). FASC-prohibited drones are defined as unmanned aircraft systems manufactured or
assembled by a covered foreign entity.
The rule will be implemented in two phases, with the initial phase in effect on November 12, 2024. This initial phase amends FAR part 40 to add new sections 40.200 through 40.202, which are to be included in all solicitations issued, contracts awarded, options exercised, or modifications made to extend the contract period of performance. During this phase, continued use of previously acquired subject drones is permitted, provided such UAS is not a deliverable under the contract.
The second phase of the interim rule goes into effect on December 22, 2025. It is more prohibitive and may
have a greater impact on university research activities. In this phase, Federal contractors (and
subcontractors) are prohibited from “using Federal funds on” subject drones, including for the
procurement and operation of FASC-prohibited UAS.

Reporting requirements for the loss, damage, or theft of federal funded research equipment
The Office of Management and Budget (OMB) is currently revising the OMB Guidance for Federal Financial Assistance. Updated 2 CFR § 200.313 – Equipment states that any loss, damage, or theft of federal funded research equipment must be investigated. The recipient or subrecipient must notify the Federal agency or pass-through entity of any loss, damage, or theft of equipment that will have an impact on the program. The effective date for the final guidance is October 1, 2024.

Executive Order: Transparency Regarding Foreign Influence at American Universities
On April 23, 2025, President Trump signed a new executive order and accompanying fact sheet that mandates full and timely disclosure of foreign funding by higher education institutions. It directs the Secretary of Education to reverse or rescind any actions by the prior administration that allow universities to obscure details regarding their foreign funding.

Updated NIH Policy on Foreign Subawards
On May 1, 2025, NIH released NOT-OD-25-104, updating NIH policies and practices utilizing foreign subawards. This comes as a response to NIH recognizing that some recipients do not accurately report on subawards consistent with Federal Funding Accountability and Transparency Act (FFATA) subaward reporting requirements, which states that recipients must report on all subawards/subcontracts/consortiums equal to or greater than $30,000.
Requirements for Research Security Programs per NSPM-33
Northeastern University Research Enterprises Services (NU-RES) serves as the centralized hub for assisting faculty in preparing and submitting their research and sponsored proposals. For matters regarding research integrity, research misconduct, and research security, the NU-RES Compliance team helps researchers navigate foreign collaborations and engagements while protecting their work from foreign influence. The NU-RES Compliance team coordinates with IT to ensure that all researchers are completing the required training and abiding by research security rules and regulations regarding controlled unclassified information (CUI), technology and export controls.
Please visit the Policies & Related Training page for information on required Research Security Program trainings.

What is Research Security?
Research security is a broad term that refers primarily to national security concerns surrounding research involving certain types of sensitive data, intellectual property, export-controlled information, and other risks. Foreign government interference threatens the U.S. science and technology (S&T) research ecosystem and the U.S. research community by undermining the principles and values foundational to the conduct of research, and the openness necessary for the research enterprise to thrive.

Northeastern University’s Research Security Program
As a global research institution, Northeastern University encourages collaboration with investigators at other institutions, both domestic and internationally. However, it is important for all investigators to be aware of and take steps to ensure that foreign influence does not threaten the integrity of research. The NU-RES Compliance team is here to help researchers navigate foreign collaborations and engagements while protecting their work from foreign influence. Northeastern University committed to providing the necessary guidance, education, and support to its faculty engaged in research. The components of Northeastern University’s research security program are below. NU-RES Compliance collaborates with various university offices to maintain a robust and up-to-date research security program.
Questions about the Research Security Program at NU? Contact our Chief Research Operations Officer, Amanda Humphrey: a.humphrey@northeastern.edu.

National Security Presidential Memorandum (NSPM) 33
The purpose of NSPM-33 is to “provide guidance to Federal departments and agencies regarding their implementation of National Security Presidential Memorandum 33 on National Security Strategy for U.S. Government-Supported Research and Development”. The guidance requires a certification from research institutions awarded more than $50 million per year in total Federal research funding confirming that they have implemented a research security program meeting the four requirements highlighted in NSPM-33: Cybersecurity, Foreign Travel Security, Research Security Training, and Export Control Training (see pgs. 18-20). Northeastern is currently working to fulfill all the requirements set forth by the National Security Presidential Memorandum (NSPM-33) and its final Guidelines for Research Security Programs at Covered Institutions as released by the Office of Science and Technology (OSTP) in July 2024.
Elements of Northeastern University’s Research Security Program
Cybersecurity
Research Compliance works heavily with Northeastern’s Office of Information Security to assist researchers in safeguarding their research data and information. For more information regarding the purpose, principles, and resources for cybersecurity at Northeastern, please visit the below websites:
Digital Persistent Identifiers (DPIs) & Digital CVs
Digital Persistent Identifiers (DPIs) and Digital CVs make it easier for researchers to create and maintain a complete and up to date record of their publications and achievements in one location, thereby streamlining the grant proposal process.
Northeastern is a full member of ORCID – Open Research and Contributor ID – a platform that provides a free and unique DPI for individuals engaged in research, scholarship, and innovation activities globally.
Science Experts Network Curriculum Vitae (SciENcv) is an electronic system created by the National Center for Biotechnology Information (NCBI) that allows researchers to assemble their professional information needed for participation in federally funded research. SciENcv is a digital CV that documents information regarding education, employment, honors, publications, and research grants. SciENcv will become mandatory for any NSF funded research beginning October 23, 2023, as outlined in the NSF PAPPG 2023.
More information on ORCID and SciENcv can be found here.
Disclosure Management
As stated above, disclosure and transparency surrounding relationships with, and research support from, foreign entities have been identified by the federal government as key to managing and protecting the security of our research. Prior to engaging in any international collaborations or outside activities Researchers are expected to:
- Be thorough and complete in accounting for all forms of research support, including from foreign sources and gifts, in the NIH’s other support, the NSF’s current and pending, and similar documentation submitted to other sponsors.
- Disclose financial interests and outside professional activities in eCD, the University’s Electronic Conflict Disclosure System annually, at the time of proposal submission through Northeastern University’s Research Enterprise Services (NU-RES), and within 30 days of acquiring new interests as required by the Policy on Conflict of Interest and Commitment.
- Activities requiring disclosure include support from foreign governments and foreign academic institutions, domestic and foreign consulting relationships, visiting positions at domestic and foreign institutions, investment in a start-up company, etc.
- Research Compliance is available to provide additional guidance on what you need to disclose and how and when to make a disclosure. In addition, faculty and staff should refresh their understanding of the Policy on Conflict of Interest and Commitment.
- Discuss any invitation for any academic appointment or position at another domestic or international institution (visiting, honorary, or other) with your Dean’s Office prior to accepting the appointment, as required by the Northeastern’s Faculty Handbook and Policy on Conflict of Interest and Commitment.
- Disclose to Research Compliance and College Dean’s Office any involvement in any foreign recruitment or “talent” programs. These programs are of particular interest to the federal government, due to the potential risk of undermining U.S. economic and security interests.
- Ensure compliance with the federal Foreign Corrupt Practices Act and the University’s Policy on the Foreign Corrupt Practices Act.
Export Controls
The Export Control Officer maintains responsibility for enforcing University-wide export compliance policies, procedures, and guidelines designed to meet or exceed the requirements of the various federal laws governing the export of goods, technology, and information, including compliance with ITAR, EAR, and OFAC regulations.
More information about Export Controls at NU can be found here.
Click here to access the Export Control Decision Tree.
Questions on export controls? Contact us at exportcontrols@northeastern.edu.
Related policies: Policy on Export Controls
Foreign Visitors & International Engagements
As a global university, Northeastern prides itself on its breadth of international students and faculty and encourages international engagements. Prior to hosting any foreign visitors and/or participating in any international collaborations or activities, faculty should review the below definitions and risk mitigation techniques.
Faculty must comply with the university’s Policy on External International Engagements and the international engagement approval process. Faculty are required to complete the International Engagements Intake Form and review these FAQs about the approval process, which includes roles and responsibilities and the rationale behind the policy. Please visit the International Engagements page to access the intake form.
Please make sure to review information regarding Foreign Talent Recruitment Programs.
Foreign Travel Security
Foreign travel regulations are currently changing, particularly around immigration, re-entry and device searching at borders. Reference Navigating a New Political Landscape: FAQ for additional information.
CBP has the authority to search an individual’s electronic devices, including mobile phone, computer, camera, or other electronic devices while being inspected for admission to the US. For individuals entering with temporary status, such as F-1, J-1, H-1B, O-1, CBP can refuse your admission to the US if you refuse to comply with a search. Lawful permanent residents can still be admitted to the US if they refuse to provide access to their electronic devices, however, permanent residents can be placed into immigration proceedings before an immigration judge if they do not comply.
International students should visit the OGS travel recommendations website: 2025 Current Travel Recommendations – Office of Global Services
NU-RES Research Compliance works with the Global Safety and Support Network to ensure that students, faculty and staff traveling internationally have the most accurate information and guidance ahead of their trip. The network provides detailed travel compliance information including travel protocols, travel tips connectivity requirements and lists of high-risk countries and high cyber risk destinations.
For international travel, students, faculty and staff are required to complete an Acknowledgement of Risk (AOR) form prior to departure, which requires disclosure of travel details, including identification of the Host or Sponsoring Institution, Organization, Department/College or Person. Information on AOR forms can be found here.
To request a loaner device (i.e. laptop) for travel to a high-risk country, please submit a ticket to the IT Service Desk here.
Travel briefings regarding research security, export controls, and/or international travel best practices, including cybersecurity safety, may be required. Travel briefings are required for travel to the following countries: Cuba, Syria, Crimean, Donetsk and Kuhansk Regions of Ukraine, Sudan, North Korea, Russia, China, and Iran.
Related policies:
Policy on Travel and Expense Reimbursement
Policy Requiring Registration of University Travel
Policy on Travel to High-Risk and Sanctioned Destinations
Policy on Computers and Mobile Devices for Travel to Destinations with Heightened Cybersecurity Risk
Research Security & Transparency
Research Security & International Collaboration Authorship FAQs
Data Management & Sharing Plans (DMSP)
Standards for the Use of Artificial Intelligence in Research at Northeastern
NIH Policy Guidance for Subaward/Consortium Written Agreements
Research Integrity & Misconduct
What is Research Integrity
Research integrity is the use of honest and verifiable methods in proposing, performing, and evaluating research; reporting research results with particular attention to adherence to rules, regulations, and guidelines; and following commonly accepted professional codes or norms (NSPM-33).
In addition to our robust RCR training program we handle other research integrity matters, including allegations of plagiarism, as well as authorship disputes. Please see this guidance document which outlines how we assess authorship disputes versus matters of plagiarism.
Research Misconduct
Northeastern University is committed to the fair and thorough investigation of Research Misconduct allegations. Research misconduct is defined in accordance with federal policy as:
- Fabrication: The making up of data or results and the recording or reporting them;
- Falsification: The manipulation of research materials, equipment or processes, or the change or omission of data or results such that the research is not accurately represented in the research record;
- Plagiarism: The appropriation of another person’s ideas, processes, results or words without giving appropriate credit.
Research misconduct does not include honest error or differences of opinion. Any individual with reason to believe that research misconduct has possibly occurred must report the matter to University officials. To report a concern, email researchcompliance@northeastern.edu or contact the EthicsPoint confidential and anonymous reporting hotline.
For information on Northeastern’s process for responding to and handling allegations of research misconduct, please read our Procedures for Responding to Alleged Research Misconduct
Related Policies
Lab Practices to Support Research Integrity
Research Compliance recommends that faculty running a lab create and utilize a Lab Policy and Expectations Manual to ensure their students are acting with integrity within their lab. More information on lab manuals can be found here.
If you are interested in having a training for your lab on Research Integrity in the Lab and/or a lab walkthrough, please contact Research Compliance.
The Office of Research Integrity (ORI) has great resources on avoiding research misconduct in the lab and can be found here.
Risk Mitigation Policies
What is risk mitigation?
Risks may affect overseas partners differently, and it is important to have policies in place that acknowledge and assess the existence of these risks. Some risk mitigation policy recommendations include:
- Undertaking regular due diligence on overseas partners,
- Recognizing the risks related to institutional autonomy and academic freedom overseas,
- Balancing requirements for local autonomy with robust, centralized risk management,
- Establishing clear reporting lines for communication with local stakeholders,
- Developing an exit strategy that is supported by a comprehensive, rules-based arrangement and high-level principles.
How does IP theft factor in?
Faculty should also be aware of intellectual property (IP) theft attempts. IP includes all exclusive rights to intellectual creations. All research can be at risk, but areas around applied research are particularly vulnerable. The consequence of research outcomes being exploited could be far greater and could result in the loss of intellectual property and misuse of research.
For individual researchers, interference with (or loss of) research is likely to limit their ability to publish first or take credit for the resulting intellectual property. This could potentially affect a researcher’s reputation and ability to demonstrate the impact of their research.
Hostile states target universities to steal personal data, research data and IP with the hopes that it could be used to help their own military, commercial and authoritarian interests.
Research funding organizations and private companies are important stakeholders when it comes to research that may result in the development of intellectual property. They may impose dissemination and/or publication restrictions to ensure the IP is protected. Some tips on limiting IP theft are below:
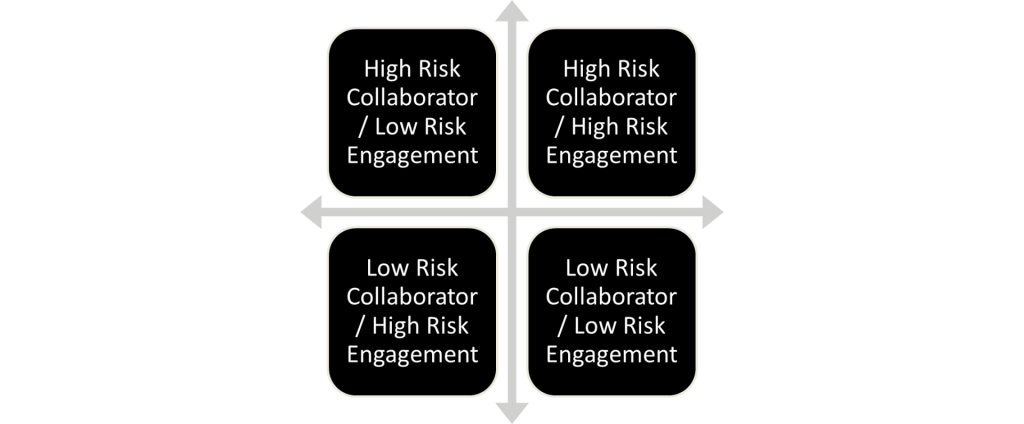
Collaboration Engagement Risk
Faculty should consider what risks come with partnering with the collaborator (ex. High risk country) and the risk of the engagement (ex. What is being studied or researched?). The below risk matrix illustrates how faculty should understand the relationship and the risks that will come from collaboration with a certain individual, institution, or company, and should serve as a starting point in the process of determining if a collaboration is low or high risk.
Agency Specific Research Security Program Requirements
Per OSTP’s Final Rule regarding Research Security Programs at covered institutions, federal agencies must stand up their own research security program guidelines. The Final Rule also states that federal agencies must develop policies regarding requirements for participants of federally funded research and development (R&D), including individuals supported by financial assistance, to be registered with a service that provides a digital persistent identifier (PID) for that individual. Federal agencies are also instructed to standardize forms for initial disclosures, integrating digital persistent identifiers for individuals applying for grants and cooperative agreement funding.
At present, the DOE, NIH, and NSF have released information regarding research security training requirements, digital persistent identifier (DPI) requirements and/or disclosure requirements.
Department of Energy (DOE)
DOE Financial Assistance Letter (FAL): Research Security Training Requirements for all R&D Financial Assistance Awards – mandatory May 1, 2025
Covered individuals listed on applications under this funding opportunity are required to certify that they have taken research security training consistent with Section 10634 of the CHIPS and Science Act of 2022.
Covered individuals must certify that they have “completed within one year of such application research security training that meets the guidelines [described in the Act]”. DOE interprets this as the 12 months immediately preceding the application date.
The DOE defines covered individual as an individual who (a) contributes in a substantive, meaningful way to the development or execution of the scope of work of a project funded by DOE or proposed for funding by DOE, and (b) is designated as a covered individual by DOE. At a minimum, DOE designates as covered individuals any principal investigator (PI); project director (PD); co-principal investigator (Co-PI); co-project director (Co-PD); project manager; and any individual regardless of title that is functionally performing as a PI, PD, Co-PI, Co-PD, or project manager.
DOE Financial Assistance Letter (FAL): Digital Persistent Identifier Requirements for Certain Individuals for Research and Development – mandatory May 1, 2025
Individuals required to submit Biographical Sketch and Current and/or Pending (Other) Support disclosures must provide a digital persistent identifier (PID) in such disclosures as part of the NOFO application. Included PIDs must meet the common/core standards specified in the NSPM33 Implementation Guidance or successor guidance (e.g., an ORCID iD). The inclusion of an individual’s PID will be optional until May 1, 2025, and mandatory thereafter.
National Institutes of Health (NIH)
NIH’s Adoption of Common Forms for Biographical Sketch and Current and Pending (Other) Support by May 25, 2025 – POSTPONED
Postponed
NIH’s adoption of the Common Form for Biographical Sketch and a new Biographical Sketch Supplement originally scheduled for May 25, 2025 is postponed. Continue to use NIH-specific format pages until further notice. Click here for more information.
NIH’s guide notice on the adoption of common forms for biographical sketch and current and pending (other) support by May 25, 2025 (NOT-OD-24-163) states that the NIH will implement the Common Forms without change to any collection fields.
NIH will require the use of a new NIH Biographical Sketch Supplement to collect the “Personal Statement,” “Contributions to Science,” and “Honors” statements.
Digital Persistent Identifier (DPI) Requirements – ORCID ID
NIH will require all Senior/Key Personnel to enter their ORCID ID into SciENcv in the Persistent Identifier (PID) section of the Common Forms.
NIH will require all Senior/Key Personnel to link their ORCID ID to their eRA Commons Personal Profile. For information on linking an ORCID ID to the eRA Commons Personal Profile see the ORCID ID topic in the eRA Commons online help.
SciENcv – Common Forms
NIH will require the use of Science Experts Network Curriculum Vitae (SciENcv) to complete Common Forms (i.e., Biographical Sketch, Current and Pending (Other) Support) and the NIH Biographical Sketch Supplement to produce digitally certified PDF(s) for use in application submission.
Current and Pending (Other) Support
NIH will no longer accept the NIH Other Support format page.
NIH will require the use of the Common Form for Current and Pending (Other) Support.
National Science Foundation (NSF)
NSF has released their draft PAPPG ’26 effective October 2025.
Research Security Training Requirements
Each individual identified as a senior/key person must certify that they have completed the requisite research security training that meets the requirements specified in PAPPG Chapter IX.C. within one year of proposal submission. See pg. II-24.
The AOR must certify that all individuals identified as senior/key personnel have completed the requisite research
security training that meets the requirements specified in PAPPG Chapter IX.C. within one year of proposal
submission.
Digital Persistent Identifier (DPI) Requirements – ORCID ID
On the Biographical Sketch Common Form, the ORCID ID field for senior/key personnel is now mandatory. See pg. II-22.
Visit https://orcid.org/ to obtain an ORCID ID.
Malign Foreign Talent Recruitment Programs (MFRTPs)
Individuals who are a current party to a Malign Foreign Talent Recruitment Program (MFTRP) are not eligible to serve as a senior/key person on an NSF proposal or on any NSF award made after May 20, 2024 (see section 10632 of the CHIPS and Science Act of 2022, (42 U.S.C. § 19040). (See also PAPPG Chapters I.E.3.b. and II.D.2.a.1 for additional information on MFTRPs.
The Biographical Sketch
and Current and Pending (Other) Support documents require the individual to certify that the information provided is accurate, current, and complete, that the individual is not a party to a malign foreign talent recruitment program.
AOR must certify that all
individuals identified as senior/key personnel have been made aware of and have complied with their responsibility under that section to certify that the individual is not a party to a malign foreign talent recruitment program. Senior/key personnel are also required to certify. See pg. II-24.
Related Government Guidance & Policies
2024
- OSTP Issues Updated Guidance to Support a Secure and Fair Research Ecosystem
- Guidelines for Federal Research Agencies Regarding Foreign Talent Recruitment Programs
- JASON Report Safeguarding the Research Enterprise (2024)
- FINAL Guidelines for Research Security Programs at Covered Institutions – OSTP (Jul 2024)
- NSF Research Security Training Modules
- DOE FAL: Research Security Training Requirements for all R&D Financial Assistance Awards (2024)
- DOE FAL: Digital Persistent Identifier Requirements for Certain Individuals for Research and Development
2023
- DRAFT Research Security Programs Standard Requirement (Feb 2023)
- JASON Report Research Program on Research Security (Mar 2023)
- COGR Matrix of Science & Security Laws, Regulations, & Policies (last updated Nov 2023)
- NSTC NSPM-33 Implementation Guidance Disclosure Requirements & Standardization (Nov 2023)
- NSPM-33 Implementation Guidance Definitions (Nov 2023)
2021-2022
- NSTC – Recommended Practices for Strengthening the Security & Integrity of America’s Science & Technology Research Enterprise (Jan 2021)
- NSPM-33 Implementation Guidance (Jan 2022)
- DOE Current & Pending Support Disclosure Requirements for Financial Assistance (Jun 2022)
- G7 Common Values and Principles on Research Security and Research Integrity (Jun 2022)
- CHIPS & Science Act (Aug 2022)
Other
- NIH Requirements for Disclosure of Other Support, Foreign Components and Conflicts of Interest
- UK Trusted Research
- DARPA Risk Matrix – Undue Foreign Influence COI or COC (Dec 2021)
- ARRP Risk Matrix – Identified Specific Actions of the Senior/Key Personnel
- NIST Research Security Resources
- Federal Research Security Issues
last updated 5.5.25